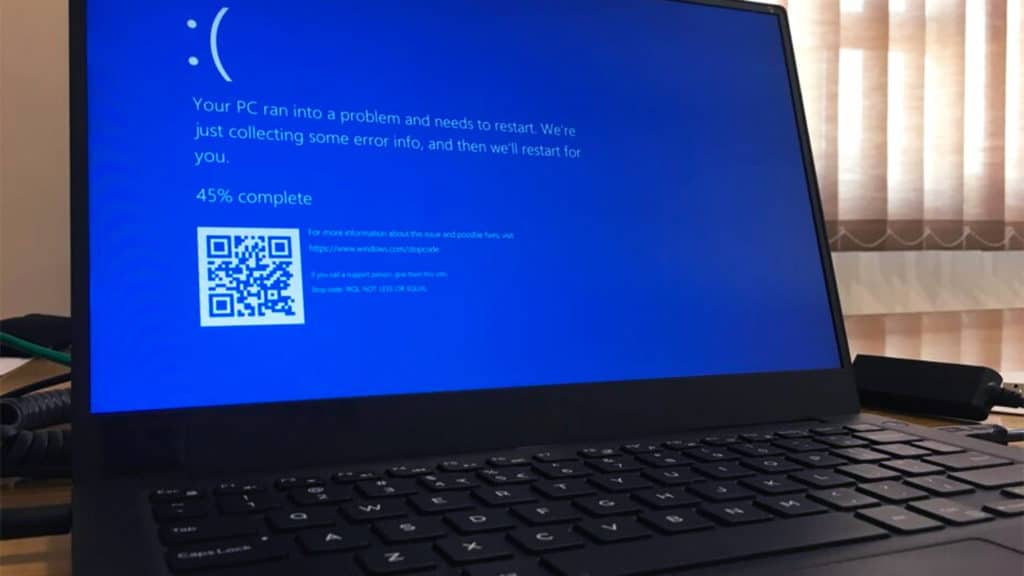
The Windows 10 update, called KB5000802, brought with it not only new features but also new bugs, reports the Windows Latest portal. This update belongs to the category of those installed automatically, which complicates the situation since Microsoft does not yet have a solution to the problems that have arisen.
KB5000802 is reported to cause an error when using printers from popular brands – Kyocera, Ricoh, Zebra and others.
Printing documents using these devices completely “crashes” the system and leads to a “blue screen of death”.
Information about Kyocera printers’ problems was confirmed by one of the Windows Latest readers, reporting that in one day, he received about 20 complaints from four different customers related to this error.
It is reported that the “blue screen of death” appears when trying to print documents from applications “office”, “Notepad” and several other services.
It is known that Microsoft has already been notified of the problems and launched an investigation into the incident – this is stated on the company’s official website.
“We are currently investigating the situation and will return to you with details when we receive more information,” Microsoft said in a statement.
At the time of this writing, the patch that fixes this bug has not been released, so users are advised to refrain from installing the KB5000802 update.
If installed automatically, you could uninstall it in the Windows settings in the “View update history” section.
In February of this year, the media reported a dangerous vulnerability in the built-in Windows antivirus Microsoft Defender. The gap was not noticed for 12 years. The vulnerability, dubbed CVE-2021-24092, lay in the BTR.sys driver. It affects versions of antivirus since 2009.
According to the researchers who identified the vulnerability, the above driver removes malicious files, replacing them with benign ones to eliminate the threat. At the same time, the system does not check this new file created as a replacement. As a result, a cybercriminal could use this flaw to force the driver to overwrite any file or even run malicious code on the system, gaining administrator rights.
Microsoft said that there is no evidence that anyone has exploited this vulnerability. There is a chance that for 12 years, it remained unknown not only to “security” but also to hackers. The company released the patch in February 2021 to fix the breach inside Microsoft Defender. The antivirus program’s default audience in modern versions of Windows is about 500 thousand people worldwide.